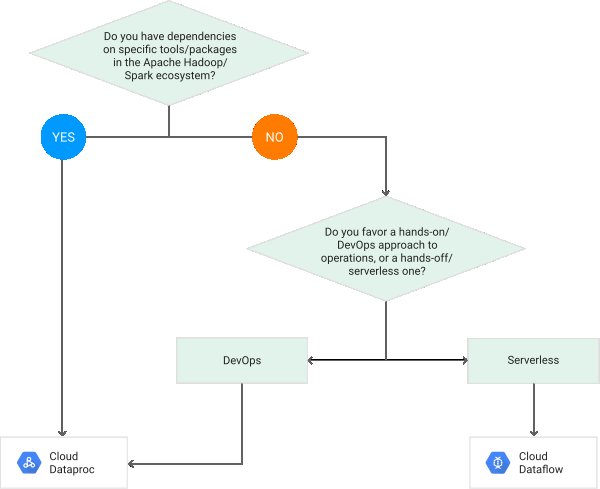
Feature Standard environment Flexible environment Instance startup time Seconds Minutes Maximum request timeout Depends on the runtime and type of scaling. 60 minutes Background threads Yes, with restrictions Yes Background processes No Yes SSH debugging No Yes Scaling Manual, Basic, Automatic Manual, Automatic Scale to zero Yes No, minimum 1 instance Writing to local disk Java 8, Java 11, Node.js, Python 3, PHP 7, Ruby, Go 1.11, and Go 1.12+ have read and write access to the /tmp directory. Python 2.7 and PHP 5.5 don't have write access to the disk. Yes, ephemeral (disk initialized on each VM startup) Modifying the runtime No Yes (through Dockerfile) Deployment time Seconds Minutes Automatic in-place security patches Yes Yes (excludes container image runtime) Access to Google Cloud APIs & Services such as Cloud Storage , Cloud SQL , Memorystore , Tasks and others. Yes Yes WebSockets No Java 8, Python 2, and PHP 5 provide a proprietary Sockets API (beta), but the API